How to Protect Yourself from the Rise of Ransomware

Ransomware attacks have escalated from small-scale operations to major assaults that target critical infrastructure, public health, and finance. Find out how to defend yourself and your business.
All it took was one compromised password for ransomware attackers to infiltrate Colonial Pipeline last month, which carries 45% of the diesel, gasoline, and jet fuel supply of the U.S. East Coast. The attack disrupted supplies for several days, causing panic buying, higher gas prices, and gas stations running out of fuel. Ultimately, the largest pipeline system in the United States decided to pay nearly USD 5 million in cryptocurrency to the criminal organization behind the attack.
“This decision was not made lightly,” a company spokesman said. “Tens of millions of Americans rely on Colonial—hospitals, emergency medical services, law enforcement agencies, fire departments, airports, truck drivers and the traveling public.”
It sounds like a narrative torn from the pages of a crime thriller novel: pitting the benefits of society’s digital transformation against villains bent on wreaking havoc for financial and political gain. Sadly—and alarmingly—ransomware attacks are not fiction but fact.
Ransomware attacks are not new, but the stakes have gotten dangerously higher. They are crippling essential services, threatening healthcare, and disrupting our daily lives. Find out why hackers are upping their game and what you can do to protect yourself and your company.
What is ransomware?
Ransomware is a type of malware (malicious software) attack that locks or encrypts files on a device. The hackers then demand ransom in exchange for decryption, threatening to sell or leak the stolen information if the ransom is not paid.
Here are seven common types of ransomware, as enumerated by Norton:
- Crypto malware. Hackers encrypt a user’s files and demand ransom. Because they use advanced encryption methods, the files cannot be decrypted without a unique key.
- Lockers. Your operating system is infected, completely locking you out of your computer or devices and making it impossible to access any files or applications.
- Scareware. Acting like an antivirus or cleaning tool, a fake software claims to have found issues with your computer that can only be resolved by paying the ransom.
- Doxware. Also known as extortionware, doxware threatens the online publication of your stolen information if you don’t pay the ransom.
- RaaS (Ransomware as a Service). In the same way that legitimate software developers lease software as a service, cybercriminals offer their ransomware to customers. The hackers take care of distributing the ransomware, collecting payments, and restoring data access in exchange for a cut of the profit.
- Mac ransomware. This type of ransomware specifically targets Apple desktops and laptops. The first known ransomware attack on Mac users occurred in 2016.
- Mobile ransomware. Ransomware usually infiltrates mobile devices through social engineering attacks. Tricking you into downloading a fake app or clicking on a spam link, it then encrypts your sensitive personal data.
Ransomware by the numbers
According to the 2021 SonicWall Cyber Threat Report, ransomware attacks have increased by 62% globally, with a 158% spike in North America. Let’s break down the numbers.
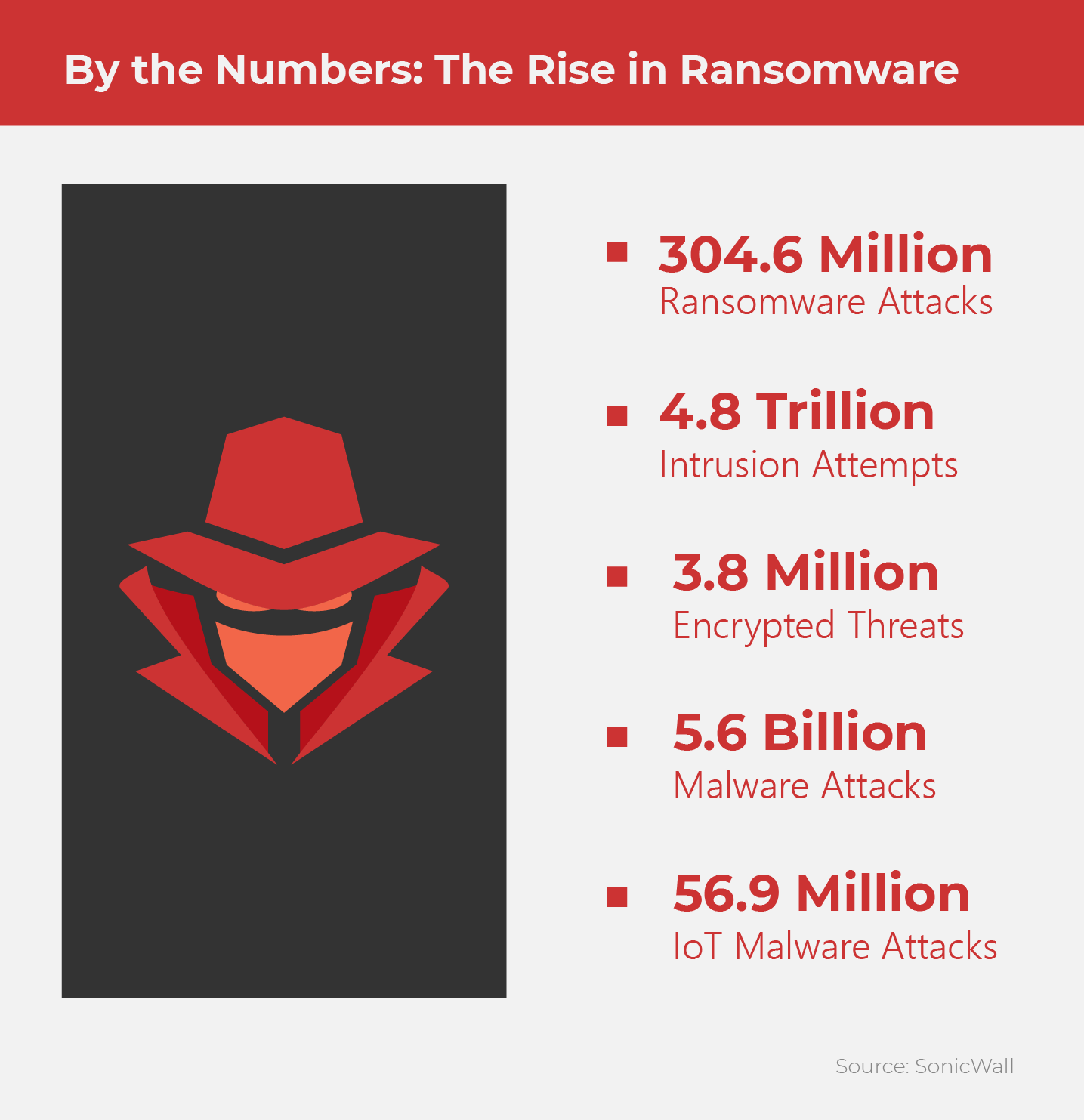

The perfect storm
The nature of the Internet—unregulated and inclusive, far-reaching and user-driven—is what makes it a fertile ground for both innovation and criminality. And with the rapid digitalization of enterprises because of COVID-19, companies now have even more access points to defend from cyberattacks.
“2020 offered a perfect storm for cybercriminals and a critical tipping point for the cyber arms race,” said SonicWall President and CEO Bill Conner. “The pandemic—along with remote work, a charged political climate, record prices of cryptocurrency, and threat actors weaponizing cloud storage and tools—drove the effectiveness and volume of cyberattacks to new highs.”
The increased reliance on digital services has accelerated software development, but most of them were not built with security as a priority. “We still have a culture of get to market, be first. We are designing code without security in mind,” Lisa Donnan, a partner at the cybersecurity private equity investor Option3Ventures, told The Guardian.
Following a cybercriminal’s trail around the World Wide Web is difficult enough, requiring cooperation between governments, especially since most ransomware attacks come from offshore.
Cryptocurrencies only add to the challenge. Decades ago, robbers and smugglers constantly faced the dilemma of moving and hiding their ill-gotten wealth. Today, digital money makes it all too easy for criminals to move millions of dollars across national borders.
The price to pay
According to Palo Alto Networks, the average ransom paid by organizations in the United States, Canada, and Europe increased from USD 115,123 in 2019 to USD 312,493 in 2020—a 170% year-on-year increase.
Chainalysis is a U.S. startup that helps governments and the private sector detect and prevent the use of cryptocurrencies in illicit activities. In their Chainalysis 2021 Crypto Crime Report, the company revealed that the total amount paid by ransomware victims increased by 311% in 2020, reaching nearly USD 350 million worth of cryptocurrency.
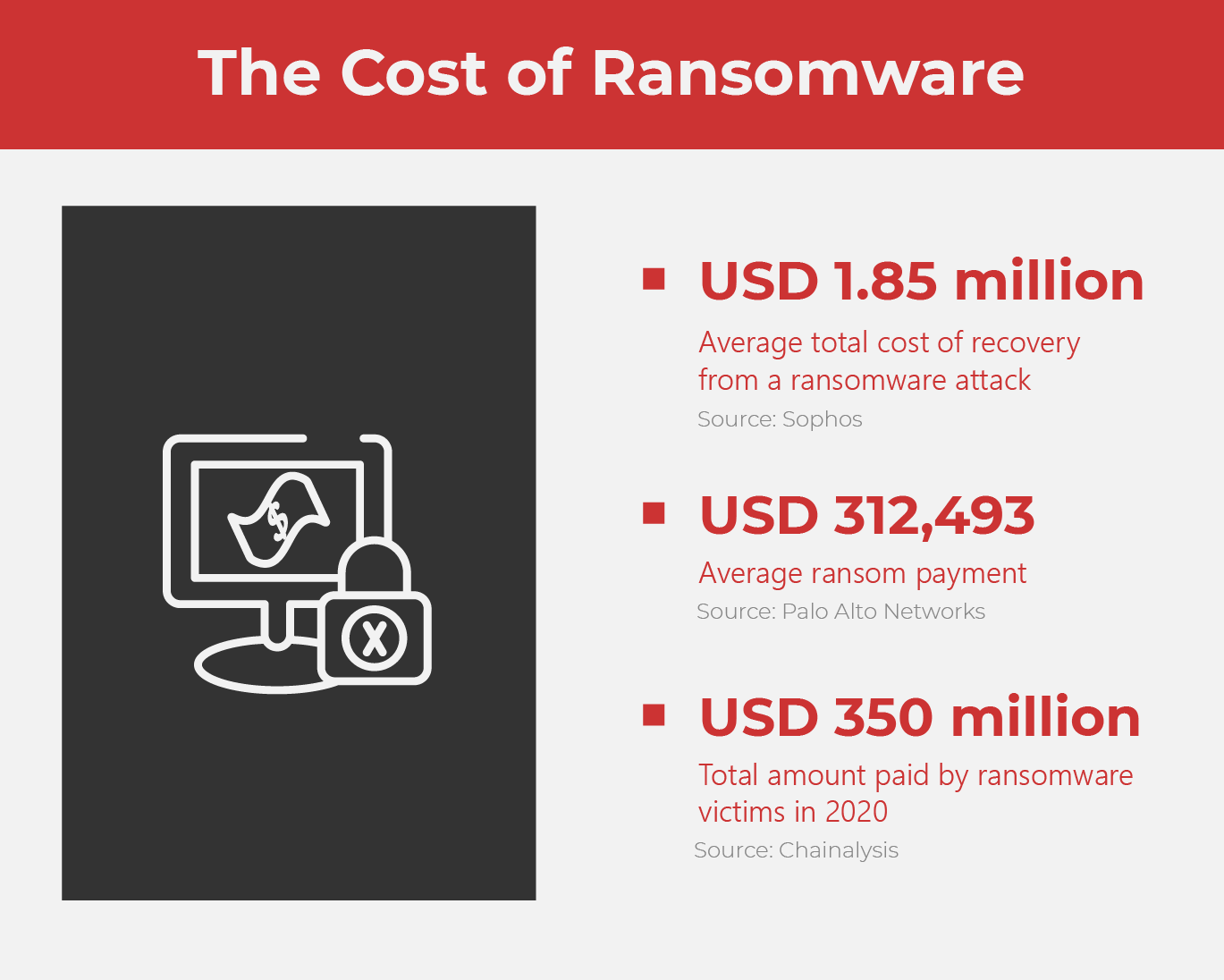
The cost of ransomware goes far beyond that of the financial. It may be primarily a profit-driven crime and it may not seem violent in the traditional sense, but it can still put lives in peril.
Ransomware has already claimed one life. Last September, a reportedly misdirected ransomware attack in a German hospital resulted in the death of a female patient in need of urgent care.
Your line of defense
The very interconnectedness we enjoy in the digital space means we have to be even more vigilant against cybersecurity threats. Here’s how you can do your part.

Defense strategies for your business
How does ransomware breach IT networks and devices? All it takes is one open door or one careless click: a user who opens phishing emails with malicious attachments or unknowingly downloads malware from an infected website.
Headlines on ransomware attacks focus on huge, high-profile companies. But, the reality is, every company is at risk. No industry, organization, or country is invulnerable. Assuming your company could be a target is the best position to take.
Here’s what you can do to protect your business from ransomware attacks, as enumerated by CO, an editorial website launched by the U.S. Chamber of Commerce.
Make sure your software is up to date. Updates from your software providers not only keep programs running smoothly but also include important security patches and updates.
Deploy layered protection. With a layered approach to security, you can block attackers at as many points as possible. Use more than one security tool, such as a firewall, anti-virus software, anti-malware software, spam filters, and cloud data loss protection. A combination gives you backup protection in case one security tool fails.
Conduct awareness training. Reduce negligence and human errors with information. “By educating them about what ransomware is, how it can infect their machines, and what they can do to stop that from happening (by not opening email attachments, being extremely wary of links in emails, etc.) you will drastically improve the most important level of defense within your organization,” said Lee Munson, Security Researcher for Comparitech.
Configure access controls. Apply the principle of least privilege (PoLP). Give users minimal access needed to fulfill their job functions, and only increase those privileges when explicitly instructed to do so by an administrator.
Use multi-factor authentication. Apart from their username and password, users must provide two or more verification factors to gain access to an account, system, or network. This could be a code sent to a separate device or a biometric verification such as a thumbprint. This decreases the likelihood of a cyber attack.
Implement strong password requirements. Here are guidelines for passwords from the National Institute for Standards and Technology (NIST):
- Be a minimum of eight characters but no more than 64 characters.
- Be able (but not required) to use all special characters.
- Avoid using sequential or repetitive characters (e.g., 1234 or aaaa).
- Restrict context-specific passwords, such as the name of the business.
- Avoid commonly used passwords (e.g., P@ssw0rd).
- Restrict the use of old passwords to avoid using credentials that may have been exposed in a data breach.
Make backups and keep a copy offline. Use the 3-2-1 rule. Have three copies of the data, use two different media, and keep one backup off-site.
Create and test an incident response plan. An incident response plan is a set of instructions to help your IT team detect, respond to, and recover from a security incident. It should include steps for recovering business operations and a business continuity strategy.
A whole-of-society response
“Cybersecurity is an area where the action or inaction of an individual has a direct link to national and international outcomes,” said Camille Stewart, a cyber fellow at Harvard University’s Belfer Center for Science and International Affairs.
All it takes is one careless click to cripple the operations of an organization. We must all be vigilant about good digital security, both at home and at work, to keep the attackers at bay.
As one of the Top 21 EMS companies in the world, IMI has over 40 years of experience in providing electronics manufacturing and technology solutions.
We are ready to support your business on a global scale.
Our proven technical expertise, worldwide reach, and vast experience in high-growth and emerging markets make us the ideal global manufacturing solutions partner.
Let's work together to build our future today.



